In the digital era, cybersecurity is a matter of extreme importance for both organizations and individuals. Cyber threats evolve with increased sophistication and frequency; traditional security systems have not, in many instances, proved useful in keeping out these threats.
Machine learning can now be an effective tool for enhancing cybersecurity along with the capability to detect and identify threats through processing large volumes of data and analyzing patterns. In this blog, we’ll explore how machine learning is being used to augment cybersecurity efforts, its key applications, and some real-world examples of its impact.
Understanding Machine Learning in Cybersecurity
Machine learning is a subfield of AI that trains algorithms to learn the patterns of data and then use those patterns to make predictions or decisions. Thus, it is possible for machine learning models to be trained in identifying malicious activities, detecting anomalies, and responding to threats in real time, as applied in the area of cybersecurity.
The greatest benefit of applying machine learning in cybersecurity is that it learns progressively and gets sharper as time passes with more input, giving it the best chance to defeat dynamic sophisticated cyber threats.
Related: Importance of Maths and Statistics in Machine Learning
Pros and Cons of Machine Learning in Cyber Security (Graphical Representation)
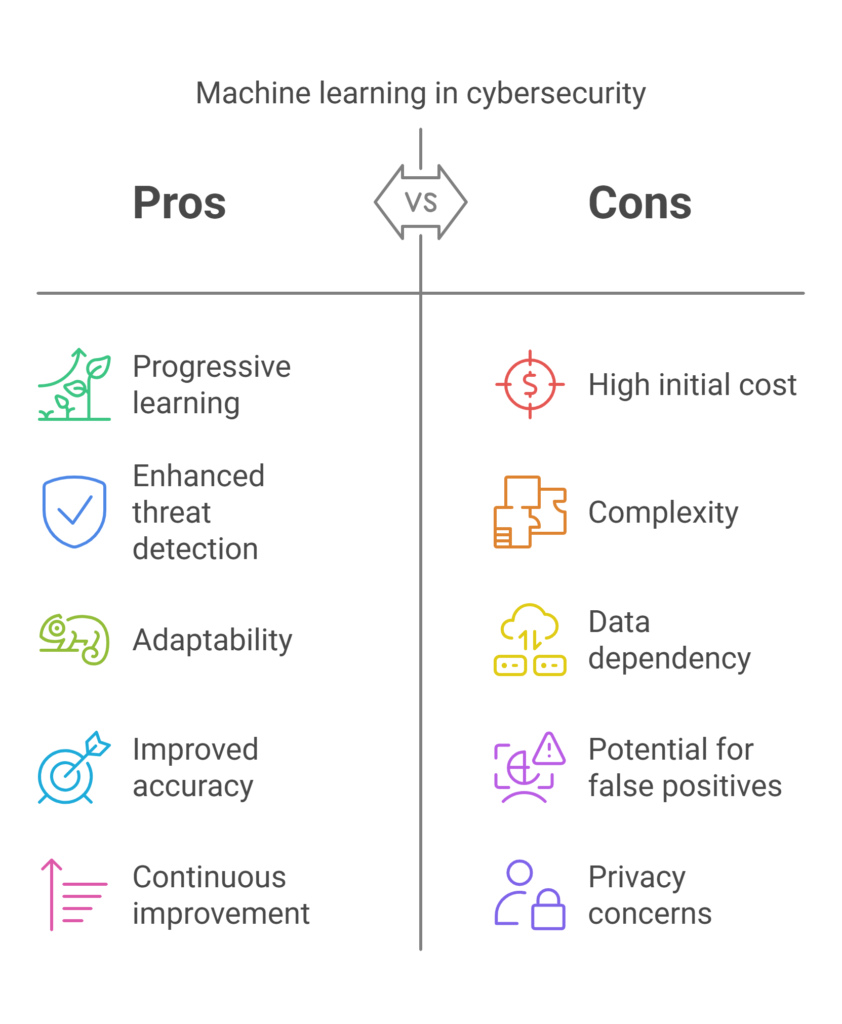
Key Applications of Machine Learning in Cybersecurity
1. IDS: Machine learning improves intrusion detection systems by analyzing the network traffic in order to track suspicious activities. Traditional IDS primarily rely on the signature-based mechanism of detection; they can detect only known attacks. Machine learning-based IDS may detect novel threats and unknown threats since the system learns how normal network traffic behaves and deviates from such behavior as a threat.
2. Malware Detection: It can analyze files and executables to identify if they have malicious code using machine learning algorithms. It identifies new and previously unseen malware variants based on known malware patterns and characteristics. It is a proactive defense against the evolving malware threats.
3. Phishing Detection: The attack has widely been used, tricking users into revealing sensitive information. In machine learning, models can take into consideration the analysis of email content, URLs, and many indicators related to the detection of phishing. The approach can learn about past phishing events and adjust according to novel tactics that have been implemented by cybercriminals.
4. Anomaly Detection: This includes the identification of unusual behavior or activities happening inside a system, which might be a sign of security threats. Machine learning-based anomaly detection techniques may comprise user behavior, network traffic, and system logs to be analyzed for the detection of anomalies. This is especially helpful in the detection of insider threats and advanced persistent threats (APTs).
5. Endpoint Protection: Machine learning enhances protection over endpoints with monitoring and analysis activities on individual devices. It detects unauthorized access, identifies the source of malware infections, and prevents data exfiltration. Machine learning-based endpoint protection solutions can adapt to new threats and provide real-time defense.
Also Read: How Machine Learning is Used in Everyday Life [2025]
Real-World Examples of Machine Learning in Cybersecurity
1. Darktrace: Cybersecurity company employing machine learning algorithms to provide real-time detection and response. Its AI-based platform, Enterprise Immune System, learns about the baseline behavior of its users, devices, and networks within an organization. Deviation from this normal behavior can thus mean that Darktrace can detect threats, for instance, insider attacks and zero-day exploits before these cause more harm.
2. Cylance: Cylance, now a BlackBerry company, extends machine learning to improve endpoint protection. The product, AI-driven CylancePROTECT, analyzes files and executables with the ultimate judgment of their maliciousness. Cylance uses the huge databases of known malware used in developing machine learning models to identify and block malicious activities in real time, even when previously unknown threats arise.
3. Google Safe Browsing: Google Safe Browsing is a service that protects users from phishing and malware attacks while surfing the internet. It uses machine learning to analyze URLs and websites for suspicious content. With its threat database constantly being updated and new threats learned from it, Google Safe Browsing alerts users and prevents them from visiting harmful websites.
4. PayPal: PayPal utilizes machine learning for fraudulent transaction detection. PayPal, with its algorithms on transaction and user behavior pattern analysis, detects anomaly patterns that can be indicators of fraud. Therefore, by employing proactive protection methods, cyber thieves are protected from users’ account details and money.
5. Splunk: Splunk is an analytics platform using machine learning that enhances the ability of SIEM. It’s a toolkit on machine learning used to build threat detection, anomaly, and predictive analytics models. Hence, it helps organizations with the identification of security incidents as well as responding to such through the application of machine learning.
Challenges and Considerations
While machine learning brings great benefits to cybersecurity and threat detection, it is not without its challenges. Some of these considerations include the following:
1. Data Quality and Quantity: Machine learning models require significant quantities of high-quality data to be effective. Incomplete, noisy, or biased data can lead to inaccuracies in predictions and false positives. Ensuring access to diverse and representative datasets is essential for the proper training of robust machine learning models.
2. Model Interpretability: Machine learning models, especially deep learning models, are highly complex and difficult to interpret. How a model arrives at a particular decision is highly important for the field of cybersecurity because it ties into trust and accountability. Thus, developing explainable AI (XAI) techniques is important in enhancing model transparency and interpretability.
3. Adversarial Attack: Another thing that is often exploited is using vulnerabilities within a machine learning model by hackers against using adversarial attacks. This implies that those in which input data is tampered with to hoodwink the machine learning model from undertaking security mechanisms put in place.
4. Integration with Available Systems: Integrating a machine learning-based solution with any existing cybersecurity systems is quite complex, resource-intensive, and time-consuming as well. Integration of the existing system of the organization with machine learning-based tools can add new complexities and vulnerabilities.
5. Continuous Learning: Cyber threats keep evolving and need machine learning models to update on the threats in real-time. The continuous updating of the model is crucial for it to maintain its effectiveness. This can be achieved by continued monitoring, data collection, and model retraining.
Conclusion
Machine learning has surfaced as a force to be reckoned with, enhancing cybersecurity and threat detection through its ability to analyze large quantities of data and detect patterns for adapting to newer threats. Its proactive and effective approach to defense from a wide range of cyber threats ranges from intrusion and malware detection, and phishing prevention, to fraud detection, among others.
The future of machine learning in cybersecurity is bright. The cybersecurity threats continue evolving and require further machine learning that will protect organizational assets, data, and reputations from various cyber threats. Organizations embracing more machine learning to invest in building robust, adaptive, and transparent models will therefore be better prepared to defend against cyber threats. We will bring together a safer, more secure future for everyone’s digital life.

